Hackers suspected of using supercomputers to mine Monero
The latest national Supercomputing service in the UK, ARCHER, first reported the security exploitation on Monday 11th May. The ARCHER team had to disable access and closed their supercomputer service to allow further investigations to occur. An update on the security incident was published on Friday, stating that diagnostic work is continuing and the group will provide a further update on the intrusion.
There were separate security incidents reported in Germany over the week. On the 14th of May, the Leibniz Supercomputing Centre reported that it had temporarily closed access to all of their High-Performance Computing (HPC) systems. The University of Dresden subsequently announced that it had shut down its Taurus supercomputer.
The Swiss National Supercomputing Centre in Zurich also announced that many of their data centers had been paralyzed in a cybersecurity incident. Within the announcement, they warn that “Several HPC and academic data centers of Europe and around the world are currently fighting against cyber-attacks and therefore had to shut down their computing infrastructure.”
London based Cado Security has released an analysis of the potential attack. They suggest a single actor or group may have been behind all the attacks in Germany, the UK, and Switzerland.
Chris Doman, Co-Founder of Cado Security, told ZDNet on Monday that attackers gained access to a supercomputing node. They then appear to have used an exploit for the CVE-2019-15666 vulnerability to gain root access to the supercomputers and then deploy an application that mined the Monero (XMR) cryptocurrency.
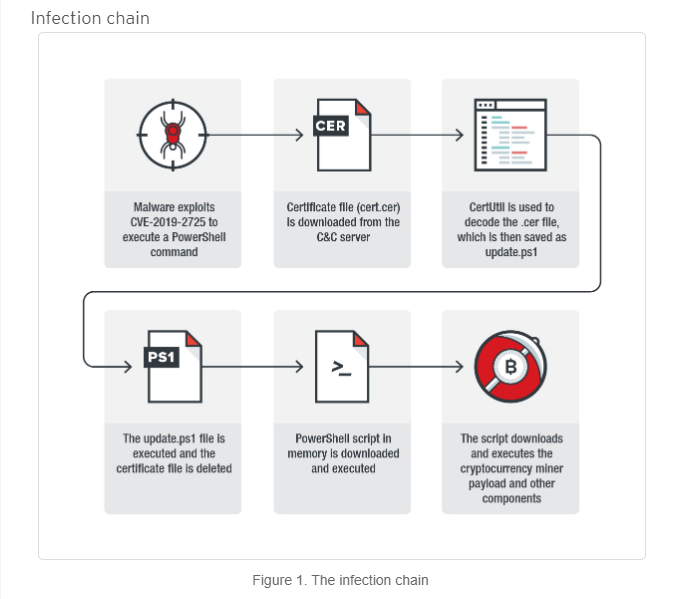
A post from June 2019 in Trend Micro Security Intelligence Blog discusses the CVE-2019-15666 vulnerability. It was first discovered in April and uses a deserialization vulnerability involving the widely used Oracle WebLogic Server.
“By using certificate files for obfuscation purposes,” the post explained, “a piece of malware can possibly evade detection since the downloaded file is in a certificate file format which is seen as normal.”
During a Livestreamed Cybersecurity panel hosted as part of the Monero networks anniversary. Dave Jevans, the CEO of California based blockchain analytic firm CipherTrace, explained that building a fully compliant monitoring system for privacy-centric blockchains like Monero is a difficult one.
Jevans points out that the onus may be on Crypto platforms where hackers choose to liquidate their acquired XMR tokens. He mentions that a potential answer is a private, secure inter-exchange transfer network, similar to the SWIFT network used by banks.
Monero has the 13th highest market capitalization of any crypto-asset on Brave New Coin’s market cap table, and the largest of any privacy-focused coin.
The project has roots dating back to 2012, and Bytecoin. Bytecoin was the first cryptocurrency based on the now ubiquitous CryptoNote application layer, which works by grouping public keys together to ensure a sender’s transaction details are obfusticated and uses ring signatures to sign transactions for anonymity.
Like Bitcoin, the Monero whitepaper has an anonymous author. The Cryptonote v 2.0 whitepaper was written by “Nicholas Van Saberhagen.” Within it, Saberhagen describes a privacy-focused alternative to the Bitcoin (BTC) vision of Peer-to-Peer Electronic cash. The whitepaper discusses the issues of Untraceability and Unlinkablitlity. It suggests that Bitcoin is only “pseudo-anonymous” and not anonymous.
Saberhagen defines an Untraceable transaction as occurring when all possible senders are equiprobable for each incoming transaction, or, there is an equal chance that any sender from the network is the originator of a transaction. Saberhagen defines an Unlinkable transaction as occurring when it is impossible to prove any two transactions were sent to the same person.
These transaction types utilize Multilayered Linkable Spontaneous Anonymous Group signatures (MLSAG), ring confidential transactions (RCT), and stealth addresses. These features enable untraceable, unlinkable, private, and analysis of resistant transactions. Unlike the Bitcoin network, the public key of both the recipient and originator of Monero is hidden on its public ledger.
OhNoCrypto
via https://www.ohnocrypto.com
Aditya Das, Khareem Sudlow
