IoT/connected Device Discovery and Security Auditing in Corporate Networks
Today's enterprise networks are complex environments with different types of wired and wireless devices being connected and disconnected. The current device discovery solutions have been mainly focused on identifying and monitoring servers, workstation PCs, laptops and infrastructure devices such as network firewalls, switches and routers, because the most valuable information assets of organizations are being stored, processed and transferred over those devices, hence making them the prime target of security breaches and intrusions.
However, a new trend has been emerging in the past four years, where attackers have been targeting purpose-built connected devices such as network printers and video conferencing systems as an entry point and data exfiltration route.
These devices cannot be identified properly by the current IT asset discovery solutions for the following main reasons:
- Proprietary protocols are often used for managing and monitoring such devices that are not known to the asset discovery solution.
- Agent-based asset discovery is not possible because most of the connected devices are resource-constrained systems with proprietary operating systems that do not allow the installation of discovery agent software on them.
Firmalyzer's IoT vulnerability assessment solution (IoTVAS) overcomes these limitations and provides:
- Accurate identification of connected device manufacturer, model name, device type, device end of life status, firmware version, and firmware release date
- Real-time Firmware bill of materials (BOM) report that lists software components and libraries inside the firmware code of each device without requiring the user to upload device firmware files.
- Identification of publicly unknown vulnerabilities of the device that includes vulnerable 3rd party components, default credentials, crypto keys, certificates, and default configuration issues
- Identification of the publicly known vulnerabilities (CVEs) of the device
IoTVAS can operate as a standalone IoT discovery and risk assessment solution or be integrated into existing IT asset discovery, network port scanners, and IT vulnerability scanning tools via IoTVAS REST API.
IoT Discovery with IoTVAS
IoTVAS identifies devices based on fingerprints derived from device network service banners. The device MAC address can also be used together with this fingerprint to improve detection accuracy, but it is not a requirement for IoTVAS, unlike the other device discovery solutions. New device fingerprints are continuously added to the IoTVAS fingerprints database, based on the incoming API request and in-house research.
At the time of writing this article, this database contains over 50,000 fingerprints for more than 2,300 device manufacturers. IoTVAS uses the following network service response and banners for fingerprint generation:
- SysDescr OID string of the SNMP service
- SysObjectID OID string of the SNMP service
- FTP service banner
- Telnet service banner
- Device hostname
- Raw response of the device webserver (http and HTTPS services)
- UPnP discovery response
- Optional MAC address of device network interface
IoTVAS would need at least one of the above features for identifying an IoT device. Network service banners can be collected by existing network port scanners or IT vulnerability scanners.
In the standalone mode, IoTVAS uses a lightweight network service identification software that probes devices on the target network to extract the aforementioned features. IoTVAS device discovery capability can also be integrated into the existing security tools via a REST API endpoint.
IoT security Audit with IoTVAS
Once a device maker, model and firmware version were identified, IoTVAS goes beyond just looking up the CVEs associated with the device and firmware version. Using Firmalyzer's proprietary firmware risk knowledge base, IoTVAS retrieves firmware bill of materials and detailed risk analysis that includes vulnerable 3rd party components in the firmware in the following categories: "network services" (UPnP server, web server, etc.), "crypto libraries" (OpenSSL, GnuTLS, etc.), "Linux OS kernel" and "client tools" (busybox, etc.).
IoTVAS also provides a list of default credentials, crypto keys embedded in the device firmware, active and expired digital certificates, weak crypto keys and certificates, and default configuration issues. This in-depth information enables security managers to proactively detect high-risk connected devices in the network and initiate mitigation efforts before these devices get compromised. This also automates the process of BOM inventory of IoT and embedded devices in the organization by eliminating the need for manual firmware download and firmware binary analysis for various IoT devices deployed in enterprise networks.
Similar to the device discovery capability, IoTVAS firmware risk assessment is also accessible via a REST API endpoint.
IoTVAS in Action
The following figure shows the risk assessment report of a Xerox network printer in the IoTVAS SaaS edition, including the firmware BOM and vulnerability details of software components.
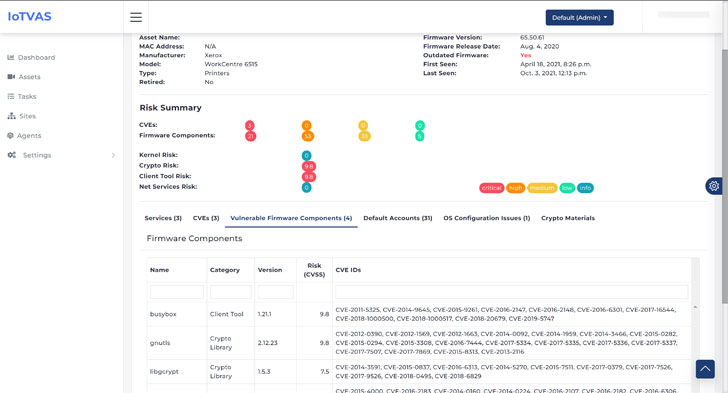 |
| Figure 1 - Device risk details page in IoTVAS SaaS |
IoTVAS API enables IT security solution providers and SecOps teams to integrate IoTVAS discovery and IoT risk audit capabilities into their existing tools and offerings. As an example, Firmalyzer developed IoTVAS plugin for the NMAP scanner that enables it to accurately discover and audit IoT devices while scanning a target network.
The next example shows how IoTVAS NSE scripts enable NMAP to accurately detect the maker, model name, the firmware version of an enterprise printer, along with its known CVEs and firmware risks. The firmware risk analysis reveals "root" and "postgres" default accounts and credentials for the "intFTP" account, a list of expired certificates and certificates with weak fingerprinting algorithm (MD5) and a default configuration of SSH daemon that allows remote root login.
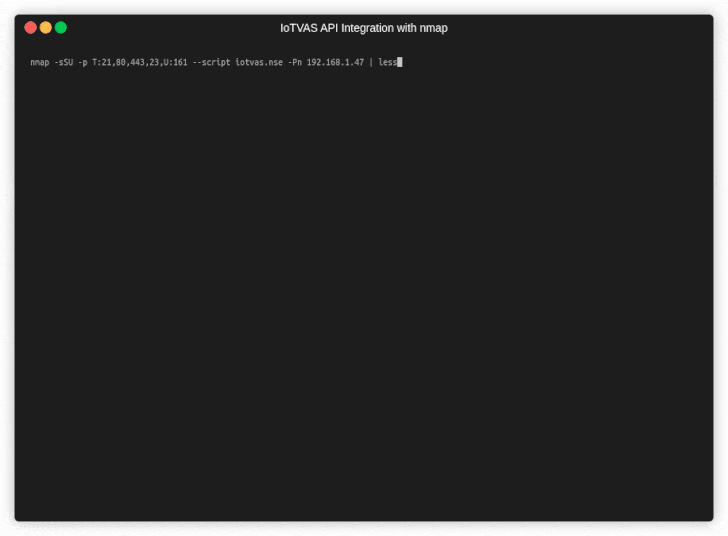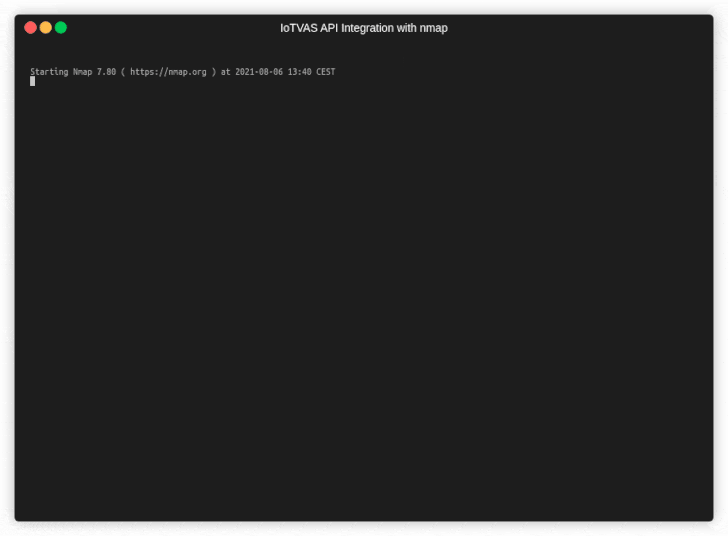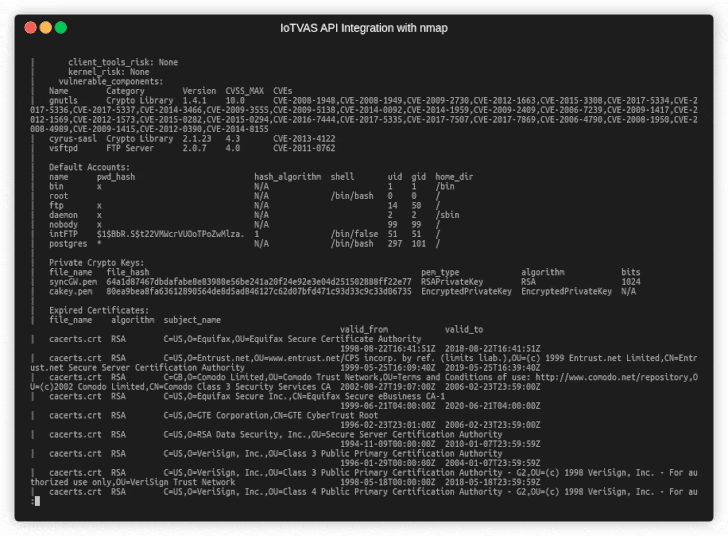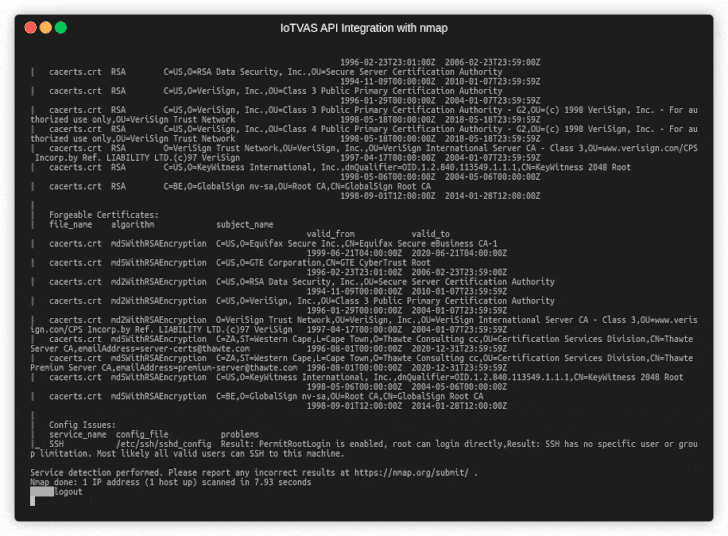 |
| Figure 2 - IoTVAS plugin for NMAP |
To get started with IoTVAS API, please register for a trial API key. The API documentation page includes a swagger UI that allows you to evaluate IoTVAS endpoints right from your browser without writing any code
If you are interested in a demo of the IoTVAS SaaS or customization, don't hesitate to get in touch with Firmalyzer for a live demonstration or a test account.
Security
via https://www.aiupnow.com
noreply@blogger.com (The Hacker News), Khareem Sudlow
